Software Security & Testing
1. what is Software Security & Testing?
Software Security & Testing is the process of ensuring that software applications are protected against threats and function correctly without vulnerabilities. It involves identifying, analyzing, and mitigating risks that could be exploited by hackers. Software security focuses on building secure applications from the ground up, while testing ensures that the software behaves as expected under various conditions. Both practices aim to prevent data breaches, unauthorized access, and software failures, ensuring the safety and reliability of applications. With the rise of cyber threats, organizations prioritize software security to protect sensitive data and user privacy.
Security testing involves several methods like static analysis (SAST), dynamic analysis (DAST), and penetration testing. Static analysis scans the source code for vulnerabilities without executing the program. Dynamic analysis tests the running application to find real-time weaknesses. Penetration testing simulates attacks to identify security gaps. Tools like OWASP ZAP, Burp Suite, and Snyk help in detecting and fixing these vulnerabilities. Common security tests include checking for SQL injection, cross-site scripting (XSS), authentication flaws, and data encryption weaknesses to ensure the software is robust and resistant to attacks.
Modern software development also emphasizes shift-left security, meaning security checks start early in the development lifecycle. This approach involves continuous testing using automated tools integrated into the CI/CD pipeline. Secure coding practices, regular audits, and compliance with standards like OWASP Top 10 and ISO/IEC 27001 ensure software integrity. As software ecosystems grow more complex with cloud computing and IoT, comprehensive security and testing strategies are essential for protecting user trust, ensuring regulatory compliance, and defending against emerging cyber threats.
2.Secure Coding Practices
Secure Coding Practices
are a set of guidelines and techniques used by developers to write software that is protected against vulnerabilities and cyberattacks. These practices help ensure that applications are resistant to exploitation by malicious actors. By following secure coding practices, developers can reduce the risk of data breaches, system compromise, and unauthorized access. Secure coding is essential across all phases of the Software Development Life Cycle (SDLC), from design to deployment, ensuring that security is built-in rather than added later.
One critical aspect of secure coding is input validation. Developers must validate and sanitize all inputs from users to prevent injection attacks such as SQL Injection (SQLi) and Cross-Site Scripting (XSS). Input validation ensures that only properly formatted data is processed by the system. For example, using parameterized queries in SQL prevents malicious code from being executed. Similarly, applying output encoding ensures that data displayed to users cannot be interpreted as code, reducing the risk of script-based attacks.
Another key practice is secure authentication and authorization. Implementing multi-factor authentication (MFA), using strong password hashing algorithms like bcrypt or PBKDF2, and enforcing least privilege access minimizes security risks. Developers should follow frameworks like the OWASP Top 10 to identify and mitigate the most common security vulnerabilities. Additionally, regular code reviews, static and dynamic analysis, and penetration testing can identify weaknesses before they reach production. Secure coding is not a one-time effort—it requires continuous monitoring, updates, and awareness of evolving threats to maintain robust software defenses.
3.Penetration Testing for Apps
Penetration Testing for Apps
for apps is a simulated cyberattack that helps identify and fix security vulnerabilities in mobile and web applications. It involves ethical hackers mimicking real-world attackers to uncover weaknesses that could be exploited. Penetration testing is crucial in today’s digital age, where sensitive user data and financial information are processed through applications. It ensures that apps are secure, compliant, and resistant to attacks before they are deployed to users.
The penetration testing process typically includes five phases: Planning and Reconnaissance, Scanning, Exploitation, Post-exploitation, and Reporting. During planning, testers gather information about the application, its architecture, and potential entry points. In the scanning phase, automated tools check for vulnerabilities like SQL injection, Cross-Site Scripting (XSS), Broken Authentication, and Insecure APIs. Exploitation involves simulating attacks to test if vulnerabilities can be exploited, while post-exploitation assesses the impact of a successful breach. Finally, a detailed report is generated, highlighting discovered vulnerabilities, their impact, and recommendations for fixing them.
Modern penetration tests also focus on mobile-specific vulnerabilities like insecure data storage, poor session management, and reverse engineering risks. Tools like OWASP ZAP, Burp Suite, and Metasploit are commonly used to identify flaws. Regular penetration testing helps organizations maintain user trust, comply with regulations (e.g., GDPR, PCI DSS), and protect against emerging threats by securing their applications against cyberattacks.

4.Automated Testing Tools
Automated Testing Tools
are essential for ensuring software quality, speed, and efficiency in modern development processes. These tools allow developers and testers to execute test cases automatically, identify bugs, and verify software functionality without manual intervention. They are widely used in agile and DevOps environments where rapid development cycles and continuous integration/continuous deployment (CI/CD) are critical. Automated testing reduces human error, increases test coverage, and ensures consistent testing across different environments. These tools are categorized into various types, including functional testing, performance testing, security testing, and unit testing, each serving a specific purpose to maintain software integrity.
Functional testing tools like Selenium, Appium, and TestComplete verify that an application’s features work correctly. Selenium is popular for web applications, supporting multiple languages such as Java, Python, and C#, allowing flexibility across various platforms. Appium specializes in mobile app testing, enabling cross-platform tests for both iOS and Android. TestComplete offers comprehensive testing capabilities for web, mobile, and desktop applications, allowing users to automate user interface interactions and validate outputs. Performance testing tools like JMeter and LoadRunner measure how a system behaves under different loads. These tools simulate user traffic and identify bottlenecks, ensuring that applications can handle real-world demands efficiently.
Security testing tools play a crucial role in safeguarding applications from vulnerabilities and cyber threats. OWASP ZAP and Burp Suite are leading tools for identifying and mitigating security risks in web applications. These tools perform automated scans, manual testing, and advanced analyses to detect weaknesses like SQL injection, cross-site scripting (XSS), and authentication flaws. Automated testing tools not only accelerate development but also enhance software quality by providing real-time feedback and allowing frequent testing cycles. Organizations adopting these tools benefit from faster delivery, improved accuracy, and better scalability, making them indispensable in today’s competitive technology landscape.
5.Secure APIs
Secure APIs
are the backbone of modern software, enabling different applications to communicate and share data. Securing APIs is crucial to protect sensitive information, prevent unauthorized access, and maintain system integrity. API security involves applying best practices such as authentication, authorization, encryption, rate limiting, and input validation. Poorly secured APIs can expose vulnerabilities that attackers can exploit, leading to data breaches, service disruptions, and compromised user privacy. Implementing robust security measures helps safeguard the API ecosystem and ensures that only legitimate users and applications can access sensitive resources.
One of the most effective ways to secure APIs is through authentication and authorization mechanisms. OAuth 2.0 and OpenID Connect are widely used protocols that provide secure access by requiring valid credentials and defining permissions. API keys offer basic security by granting access to authorized users, but for advanced protection, JSON Web Tokens (JWT) are often used. JWTs provide a stateless and encrypted way to authenticate users and verify claims. Implementing role-based access control (RBAC) ensures that users only access the parts of the API that they are authorized for, reducing the risk of data leaks.
Data encryption and input validation further strengthen API security. Secure APIs use HTTPS (SSL/TLS) to encrypt data during transmission, protecting it from eavesdropping and man-in-the-middle attacks. Input validation prevents common vulnerabilities like SQL injection and cross-site scripting (XSS) by sanitizing and verifying incoming data. Additionally, rate limiting and throttling control the number of requests a client can make within a specific timeframe, protecting against DDoS (Distributed Denial of Service) attacks. Regular security testing, including penetration testing and vulnerability scanning, helps identify and mitigate weaknesses, ensuring APIs remain secure as technology evolves.
6.Threat Modeling in Software Development
Threat Modeling in Software Development
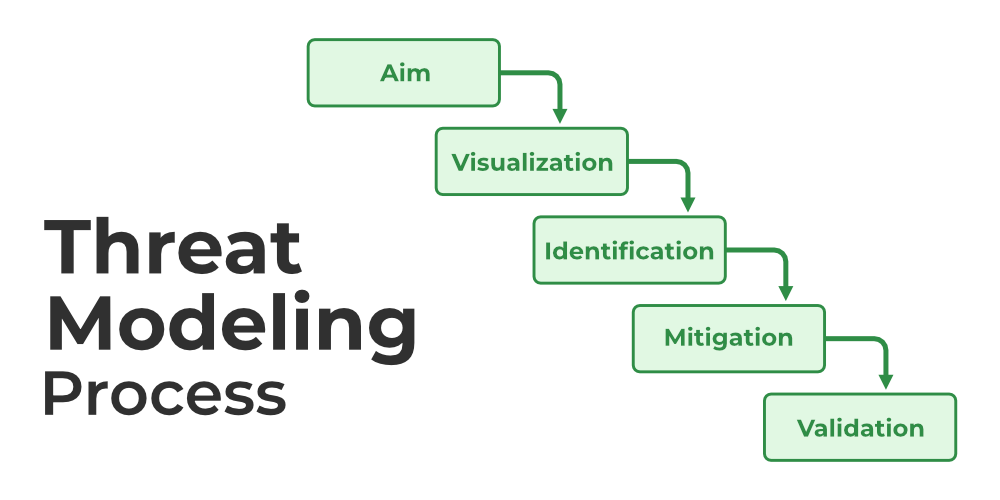
is a structured process used to identify, analyze, and mitigate potential security threats in software systems. It helps developers and security teams understand how an attacker might exploit vulnerabilities and implement protective measures. This process typically involves four key steps: identifying assets, assessing potential threats, analyzing vulnerabilities, and implementing mitigations. By integrating threat modeling early in the software development lifecycle (SDLC), organizations can proactively address security risks, reduce vulnerabilities, and protect sensitive data.
A common framework for threat modeling is STRIDE, which categorizes threats into Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service (DoS), and Elevation of Privilege. For instance, spoofing involves impersonating users to gain unauthorized access, while tampering refers to modifying data without permission. Teams use Data Flow Diagrams (DFDs) to map how data moves through the system, identify potential entry points, and determine areas where security controls are necessary. Attack trees and MITRE ATT&CK frameworks are also used to visualize and prioritize threats systematically.
Implementing threat modeling requires a collaborative approach between developers, security experts, and stakeholders. It should be a continuous practice rather than a one-time activity. Automated tools like Microsoft Threat Modeling Tool and OWASP Threat Dragon assist in identifying risks efficiently. Regularly updating threat models as systems evolve ensures emerging threats are addressed. By adopting threat modeling, organizations can strengthen their defense posture, comply with security standards (like ISO 27001 and GDPR), and reduce the likelihood of costly security breaches.
7.DevSecOps
DevSecOps
is a methodology that integrates security practices into the software development lifecycle (SDLC). It extends the principles of DevOps by embedding security measures throughout the development process rather than addressing them after the software is built. This proactive approach ensures that security is treated as a shared responsibility among development, operations, and security teams. The primary goal of DevSecOps is to deliver secure software faster by automating security checks and reducing vulnerabilities before they reach production.
In DevSecOps, security is implemented through automation and continuous integration/continuous deployment (CI/CD) pipelines. Security tools such as static code analysis (SAST), dynamic application security testing (DAST), and container scanning are integrated into the CI/CD workflow to identify and fix vulnerabilities in real-time. For example, tools like SonarQube, OWASP ZAP, and Aqua Security help in detecting and remediating code-level and infrastructure risks. This continuous monitoring and feedback loop ensures that every code change is scanned for security flaws without delaying delivery.
A successful DevSecOps culture involves collaboration, training, and process automation. Developers receive security training to write secure code, while security teams create automated checks and policies to enforce compliance. By adopting "shift-left" principles—addressing security issues early in the SDLC—organizations reduce the cost of fixing vulnerabilities later. DevSecOps supports compliance with frameworks like ISO 27001, GDPR, and NIST. Overall, it helps deliver faster, safer software while maintaining operational agility and robust security standards.
8.Static & Dynamic Code Analysis
Static & Dynamic Code Analysis are two essential techniques used to identify and fix vulnerabilities in software during the development process. Both approaches play a crucial role in ensuring the security, performance, and reliability of applications, but they differ in their methods and timing within the software development lifecycle (SDLC). By integrating these analyses, organizations can detect and resolve potential threats before they reach production environments.
Static code analysis involves examining the source code without executing the program. This method identifies vulnerabilities, coding errors, and compliance violations early in the development cycle. It is performed using Static Application Security Testing (SAST) tools like SonarQube, Checkmarx, and Bandit. Static analysis helps detect common issues like SQL injection, cross-site scripting (XSS), buffer overflows, and insecure API usage. Since the code is not run, static analysis is fast and provides immediate feedback to developers, reducing the cost and time of fixing issues later.
Dynamic code analysis, on the other hand, examines a running application to identify vulnerabilities during its execution. This method is performed using Dynamic Application Security Testing (DAST) tools like OWASP ZAP, Burp Suite, and Nikto. Dynamic analysis detects real-time issues such as authentication flaws, session management errors, and runtime vulnerabilities that static analysis may overlook. It is particularly useful for testing web applications and APIs in a live or staging environment to simulate real-world attacks and analyze system behavior under various conditions.
Dynamic code analysis, on the other hand, examines a running application to identify vulnerabilities during its execution. This method is performed using Dynamic Application Security Testing (DAST) tools like OWASP ZAP, Burp Suite, and Nikto. Dynamic analysis detects real-time issues such as authentication flaws, session management errors, and runtime vulnerabilities that static analysis may overlook. It is particularly useful for testing web applications and APIs in a live or staging environment to simulate real-world attacks and analyze system behavior under various conditions.
Static & Dynamic Code Analysis are two essential techniques used to identify and fix vulnerabilities in software during the development process. Both approaches play a crucial role in ensuring the security, performance, and reliability of applications, but they differ in their methods and timing within the software development lifecycle (SDLC). By integrating these analyses, organizations can detect and resolve potential threats before they reach production environments.
Static code analysis involves examining the source code without executing the program. This method identifies vulnerabilities, coding errors, and compliance violations early in the development cycle. It is performed using Static Application Security Testing (SAST) tools like SonarQube, Checkmarx, and Bandit. Static analysis helps detect common issues like SQL injection, cross-site scripting (XSS), buffer overflows, and insecure API usage. Since the code is not run, static analysis is fast and provides immediate feedback to developers, reducing the cost and time of fixing issues later.
Dynamic code analysis, on the other hand, examines a running application to identify vulnerabilities during its execution. This method is performed using Dynamic Application Security Testing (DAST) tools like OWASP ZAP, Burp Suite, and Nikto. Dynamic analysis detects real-time issues such as authentication flaws, session management errors, and runtime vulnerabilities that static analysis may overlook. It is particularly useful for testing web applications and APIs in a live or staging environment to simulate real-world attacks and analyze system behavior under various conditions.
Dynamic code analysis, on the other hand, examines a running application to identify vulnerabilities during its execution. This method is performed using Dynamic Application Security Testing (DAST) tools like OWASP ZAP, Burp Suite, and Nikto. Dynamic analysis detects real-time issues such as authentication flaws, session management errors, and runtime vulnerabilities that static analysis may overlook. It is particularly useful for testing web applications and APIs in a live or staging environment to simulate real-world attacks and analyze system behavior under various conditions.

Comments